By Sreebhadra Sinil | May 19, 2025

In a world where almost everything happens online—from banking to healthcare to social connections—keeping digital spaces secure is more important than ever.
Access control in network security has become an essential focus for individuals, businesses, and government agencies alike.
As we increasingly rely on computers, mobile devices, cloud platforms, and interconnected networks, controlling who can enter these digital spaces and what they can do once inside has grown into a complex but vital task.
Access control is fundamentally about establishing clear rules, mechanisms, and procedures that decide who among a network’s users is authorized to access specific information, applications, or systems—and who is not.
This function forms the backbone of cybersecurity strategies aimed at protecting sensitive data and preventing unauthorized breaches.
The importance of access control cannot be overstated, especially as cyber threats become more sophisticated and frequent.
Hackers are no longer limited to opportunistic attacks; instead, they use targeted methods to exploit vulnerabilities, gain illicit entry, and cause significant damage.
Data breaches, ransomware attacks, insider threats, and credential thefts pose constant risks to organizations of all sizes.
In this environment, simply having a network connected to the internet is no longer enough.
Strong access control policies and technologies act as the first line of defense to ensure that only legitimate users can navigate through the network.
This reduces the risk of cyber intrusions that can compromise business continuity, privacy, and trust.
At its core, access control involves defining “who” can access “what” resources, under “which” conditions.
These conditions are set according to policies that consider factors such as the user’s role, the sensitivity of the data, the device they are using, and even the time or location of the access request.
This layered approach helps organizations enforce the principle of least privilege—granting users the minimum permissions necessary to perform their duties.
It limits exposure to potential threats and ensures tighter security.
Access control is not a one-size-fits-all solution but a tailored framework that fits the unique needs and risk profiles of each organization.
Furthermore, the explosion of cloud computing and remote work has dramatically expanded the boundaries of traditional network perimeters.
Employees no longer work solely within secure office networks; instead, they connect from home, public Wi-Fi, or mobile hotspots.
This shift challenges conventional access control methods that were primarily designed for static environments.
Today, security teams must adopt more dynamic and context-aware access control systems that evaluate not just identity credentials but also environmental factors.
These include device health, user location, time of access, and behavioral patterns.
This evolution marks a significant advancement in how access control operates, making it more adaptive and responsive to emerging threats.
Implementing access control involves multiple layers and technologies.
These include authentication mechanisms like passwords, biometrics, and multi-factor authentication (MFA), as well as authorization systems that determine permissions.
It also incorporates logging and auditing to track access events for compliance and forensic analysis.
Together, these components create a holistic defense strategy that aligns with regulatory requirements such as GDPR, HIPAA, and PCI-DSS.
These regulations mandate strict controls over who can access sensitive information.
Moreover, as cyberattacks grow in complexity, modern access control systems increasingly integrate artificial intelligence and machine learning.
These intelligent systems monitor user behavior continuously, identify anomalies, and dynamically adjust access privileges.
This helps prevent unauthorized activities before they escalate.
This proactive security posture helps organizations stay one step ahead of attackers.
It provides not only protection but also operational efficiency.
Understanding Access Control in Network Security
Access control in network security is the general process of limiting access to information, systems, and network resources. Permitting only authorized users and devices to interact with sensitive digital resources is its primary role. This is the first line of defense against insider threat, unauthorized access, cyberattacks and data breaches. Secure access control for network security offers a secure safeguard of confidentiality, integrity, and availability since only authenticated users and authorized roles have access to systems storing sensitive primary data.
Types of Access Control in Network Security
There are several key models of access control within network security, each providing different levels of flexibility, control, and security. Understanding these models helps organizations choose the best fit for their specific needs.
1. Discretionary Access Control (DAC)
- Ownership-Based: The owner of the resource (file, data, or system) has the authority to grant or revoke access permissions.
- Flexible Control: Users can share access with others at their discretion, making it easy to manage in small environments.
- Common Use: Often found in personal computers, small businesses, and less regulated environments.
- Security Risk: Because permissions are user-controlled, it can lead to accidental or intentional over-sharing, increasing vulnerability.
2. Mandatory Access Control (MAC)
- Centralized Authority: A strict, centralized security policy determines access, based on classification levels or security labels assigned to both users and data.
- High Security: Users can only access data for which they have proper clearance; they cannot override access policies.
- Typical Usage: Widely used in military, government, and other high-security environments where confidentiality is critical.
- Reduced Flexibility: The rigid nature of MAC limits flexibility but strengthens protection against unauthorized access.
3. Role-Based Access Control (RBAC)
- Role-Centric: Access permissions are assigned to specific roles rather than individual users. Users gain permissions based on their assigned roles.
- Simplified Management: Ideal for organizations with clear job functions and responsibilities, reducing administrative overhead.
- Scalable and Flexible: Roles can be easily modified or created to match evolving business needs without reassigning permissions to individual users.
- Common in Enterprises: Heavily used in corporate settings for managing access across departments and teams.
4. Attribute-Based Access Control (ABAC)
- Context-Aware: Access decisions are made based on multiple attributes such as user identity, device type, location, time of access, and other environmental factors.
- Fine-Grained Control: Allows highly detailed and dynamic access policies that adapt to changing contexts.
- Enhanced Security: Ensures access is granted only when all relevant conditions and attributes meet policy requirements.
- Ideal for Complex Environments: Perfect for cloud computing, remote workforces, and organizations requiring adaptive security controls.
Importance of Access Control in Network Security
The role of access control in network security cannot be exaggerated. It is necessary for:
• Data Protection: It safeguards sensitive data (personal data, financial data, intellectual property) from abuse.
• Regulatory compliance: Policies such as GDPR, HIPAA, and PCI-DSS enforce rigorous access control for network security.
• Threat reduction: It keeps it out by only letting in what is needed, and therefore avoids the threat of internal and/or external threats.
• Operational efficiency: Provides users with the authority to perform their tasks without disrupting overall security.
All in all, these benefits underscore how critical access control in network security is in the defense of digital spaces.
Implementing Effective Access Control in Network Security
To improve access control in network security, organizations may implement a number of best practices:
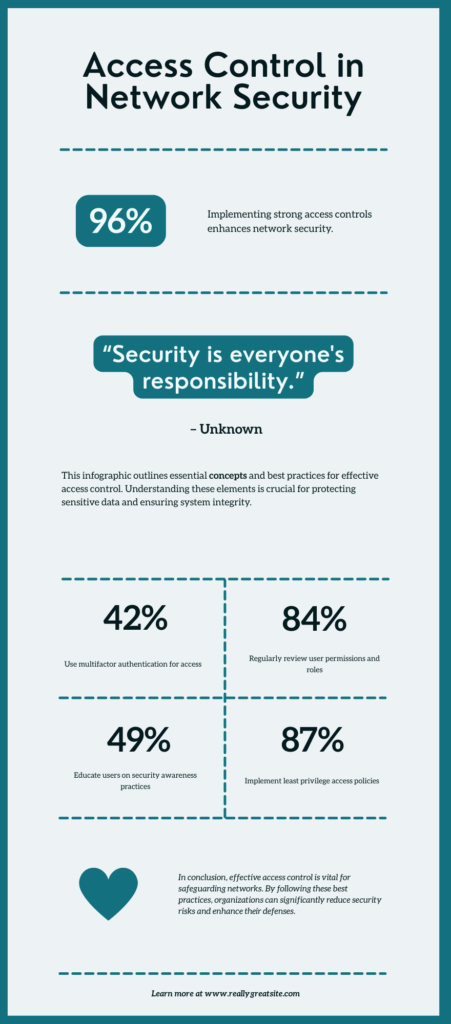
1. To have clear rules of access: Determine who all must access what resources and why.
2. Utilize the concept of least privilege (PoLP): Provide the users with the least level of access necessary for their purpose.
3. Enact multi-factor authentication (MFA): Include extra authentication layers to minimize the threat of stolen credentials.
4. Regularly review access: Regularly review user access to eliminate stale or no longer needed permissions.
5. Roll out identity and access management (IAM) solutions: Centralize user authentication and access control to simplify account provisioning and revocation.
6. Enforce Network Segmentation: Create isolated domains to restrict lateral movement in case of a breach.
7. Monitor and Log Access Activity: Keep track of who accessed what and when to support compliance and incident response.
8. Apply RBAC Where Possible: Assign roles based on job functions, making access management and policy enforcement easier.
These measures greatly enhance access control in network security infrastructure.
Obstacles to Enforcing Access Control in Network Security
In spite of its fundamental significance, enforcing access control in network security is affected with a number of challenges:
• Complexity of large network: Handling thousands of users and interconnected systems can make access governance complicated.
• Resistance from users: Workers can find strict access controls inconvenient which could impact productivity.
•Dynamic work environments: Cloud computing and remote work bring in new factors that are difficult for traditional models of access control to handle.
•Shadow IT: Unauthorized Devices and applications create unmanaged access points.
To counter these challenges, embracing flexible models such as Zero Trust Architecture becomes imperative. These frameworks improve access control in network security by adopting no default trust, not even within the network boundary.
AI and Automation Improving Access Control in Network Security
New advances in automation and artificial intelligence (AI) are transforming the way network security access control is dealt with. These technologies enable real-time decision-making as well as active risk prevention:
•Behavioral Analytics: AI can identify unusual user behavior that could represent security violations.
•Automated Access Provisioning: Grant or withdraw permissions automatically according to pre-configured policies.
•Rapid Threat Detection: AI solutions can rapidly detect and quarantine compromised accounts, minimizing harm.
The incorporation of AI not only makes access control more efficient in network security but also lightens the workload of IT staff.
Best Practices for Enhancing Access Control in Network Security
To construct strong network defenses, organizations need to include these best practices:
• Zero Trust Deployment: Never trust any device or user by default; rather, relentlessly authenticate access requests.
• Employee Education: Educate employees on secure password habits and identifying phishing attempts.
• Secure Communication Channels: Employ VPNs and encryption to secure data in motion.
• Device Authentication: Authenticate only devices that are permitted to access network resources.
• Incident Response Procedures: Establish and test incident response plans for security incidents related to access.
These elements taken together advance the trustworthiness of access control as a function of network security across a variety of environments.
Future Directions in Access Control in Network Security
The evolution of access control as a core function in network security is gaining significant momentum, driven by rapid technological advancements and shifting security paradigms. As organizations strive to protect increasingly complex digital infrastructures, new trends are emerging that promise to reshape how access is managed, verified, and monitored. These innovations not only aim to enhance security but also improve user autonomy, operational flexibility, and trustworthiness across digital environments. Understanding these emerging trends is crucial for businesses looking to future-proof their access control strategies and defend against sophisticated cyber threats.
• Decentralized Identity Management:
Traditional identity systems rely heavily on centralized authorities, which often become single points of failure and attractive targets for attackers. Decentralized identity management, by contrast, empowers users to own and control their digital identities independently of any central authority. Through technologies like blockchain-based self-sovereign identity frameworks and decentralized identifiers (DIDs), users can securely authenticate themselves without constantly exposing sensitive personal data to multiple third parties. This approach reduces the risk of identity theft and unauthorized access while enhancing privacy and enabling seamless cross-platform authentication.
• Advanced Biometrics:
The use of biometrics in access control is evolving beyond simple fingerprint scanners to include sophisticated modalities such as facial recognition, iris scanning, voice recognition, and behavioral biometrics. These technologies leverage unique physiological and behavioral characteristics to authenticate users with high accuracy. Advanced biometrics not only increase security by making unauthorized access more difficult but also improve user convenience by offering fast, often contactless authentication methods. Their growing integration into mobile devices, workplace entry systems, and cloud services demonstrates their vital role in strengthening access controls.
• Context-Aware Access:
Context-aware access control adds a dynamic dimension to security by evaluating the circumstances surrounding each access attempt. Instead of relying solely on static credentials like passwords or tokens, systems analyze contextual factors such as the user’s geographic location, device being used, network environment, and time of access. For example, an access request from an unrecognized device late at night in an unusual location may trigger additional authentication steps or be denied altogether. This real-time, adaptive decision-making reduces risks linked to compromised credentials and ensures that access permissions are aligned with the current risk level.
• Blockchain Integration:
Blockchain technology offers a powerful solution for securing access records by providing a decentralized, immutable ledger that records every access event transparently and securely. The distributed nature of blockchain prevents tampering or deletion of logs, ensuring the integrity and traceability of access activities. This tamper-proof audit trail helps organizations comply with regulatory requirements, facilitates forensic investigations, and builds greater trust in access control systems. By integrating blockchain into identity and access management frameworks, businesses can achieve higher accountability and enhanced security assurance.
All these innovations will further enhance and secure access control in network security in the years to come.

Conclusion
Network security access control is undeniably one of the cornerstones in safeguarding today’s complex digital infrastructures. As organizations increasingly rely on interconnected systems, cloud services, and remote access, the traditional perimeter-based security models are no longer sufficient. Implementing robust access control in network security mechanisms ensures that only authorized users and devices can interact with critical resources, significantly minimizing the attack surface. This is not merely about setting up firewalls or password policies—it’s about weaving a comprehensive strategy that integrates advanced technologies like artificial intelligence and machine learning, which can detect anomalies, predict threats, and adapt defenses in real-time.
But technology alone isn’t the silver bullet. Establishing a pervasive culture of security awareness throughout every level of your organization is equally vital. Employees and stakeholders must be educated about the risks and trained in best practices, such as recognizing phishing attempts, maintaining strong credentials, and adhering to access protocols. When security becomes part of the organizational DNA, human error—a leading cause of breaches—can be drastically reduced, complementing technological safeguards.
Looking ahead, the digital ecosystem is only set to grow more complex, interconnected, and vulnerable. The rise of IoT devices, cloud-native applications, and hybrid work models introduces new vectors for potential breaches, making the task of access control in network security ever more challenging. This evolving landscape demands smart, flexible, and scalable solutions that not only protect but also anticipate emerging threats. AI-powered identity and access management systems can continuously learn from network behaviors, enforce dynamic policies, and automate responses to suspicious activities, offering a proactive defense rather than a reactive one.
Moreover, compliance requirements and industry regulations are becoming increasingly stringent, mandating businesses to adopt more rigorous access controls. Failing to comply can lead to costly penalties, reputational damage, and loss of customer trust. Hence, investing in a future-ready access control framework aligns not just with security best practices but also with business continuity and growth.
In essence, network security access control isn’t a one-time project; it’s an ongoing commitment to resilience and vigilance. It requires regular assessments, updates, and a willingness to embrace new technologies and methodologies as they evolve. Those organizations that prioritize access control today will find themselves better positioned to withstand cyberattacks tomorrow and beyond.
So ask yourself—do you believe your current access control plan is strong enough? It’s never too soon to make your defenses harder and strengthen your network security position. Because in the world of cybersecurity, preparedness is the best form of protection. The future is digital, and with it comes the responsibility to secure what matters most—your digital assets, your data, and your trust.
